Data Access Governance: Tooling to gain insight into current NTFS rights within the network
Navigating the complexities of NTFS permissions can be challenging, especially when ensuring proper Data Access Governance. In this post, we have evaluated 18 of the top tools on the market to help you make a well-informed decision. From features to performance, dive in and see how the top tools stack up and why we believe our tool stands out!
- 1. Introduction
- 2. Standard Windows tooling
- 3. Largescale software packages
- 4. Focused commercial tooling
- 5. Freeware
- 6. Conclusion
- 7. Approach with Perdemia's Permission Analyzer
1. Introduction
It is common knowledge that most cases of data theft occur within the organization. No hacks from the outside, but people within the organization who (accidentally) unfairly have access to sensitive data. Apart from the financial damage, damage to reputation, this leads in many cases to legal violations, loss of intellectual property and problems in the customer relationships. See this article on Digital Guardian from this year in which 47 data security experts share their vision when it comes to protecting data and how the greatest risks come from within the organization. Employees are already cleared for most security measures and are already logged on to the network domain, they know the organization and can easily ask for additional rights. Although external attacks partly focus on weaknesses in the system, many hackers focus on existing authorized credentials through social engineering and phishing emails.One of the complexities in the protection of data is that the solution doesn't rely on just one department. The business departments have the knowledge about the necessary authorizations and the sensitivity of data, while the IT Department has the knowledge about user groups, the rights structure and tooling. Both parties must find a balance between protection of data and supporting the business processes in which constant changes take place with accompanying pressure to ease the security principles. Who is now responsible for the protection of data and monitoring of policy?
Each organization starts with a clean design in the form of user groups, directory structures and processes, but as time passes this design blurs. Users request additional rights, projects use new approaches, departments reorganize or network data is restructured. Gradually there is a proliferation of rights and no longer can they be checked to see if the original design still applies, with all its consequences. Is the data still sufficiently protected? Do the defined groups still have the correct rights? And are temporarily acquired rights and group changes properly cleaned up? In other words, can we still rely on the design on paper with which strategic business goals, financial results, personal data, internal reviews and intellectual property are protected? We call this Data Access Governance (DAG). Many companies in recent years have given priority to DAG and the protection of 'unstructured data', such as spreadsheets, presentations, documents and other data made by employees carrying out their day to day work. Gartner indicates that 80% of all data is unstructured. The first step in protecting this is the clarification, clean-up and organization of the current data and rights granted.
In this article we look at how we can get more insight by means of tooling in the protection of data and what the concerns are and gaining an overview of network rights. We compare 18 of the most common tools surrounding NTFS rights and look at how Data Access Governance in these tools is supported. Each of these tools is being tested in our test environment consisting of a Domain Controller running Windows Server 2022 on an Intel Core i7-3520M with 16 GB memory, Active Directory containing a 10,000 users and groups and a file server with 500,000 files and directories. Each of the tools is assessed for reporting capabilities for NTFS rights, strengths and weaknesses and the way in which the below information requirements are addressed. In the last chapter, we show how Perdemia's Permission Analyzer can be used to support Data Access Governance.
Information requirements
If we wish to gain insight into the current access rights, the following questions arise:- What are the effective rights for a specific user or group (including rights obtained through nested group memberships)?
- Where do the rights come from for a user? Through which folders and group memberships are the rights granted?
- Which groups and users have indirect access to a specific folder?
- What happens if someone is placed in a group?
- What are the rights for all users of a specific group and what exceptions apply?
- Can we validate and maintain consistency in the original security design for data access?
2. Standard Windows tooling
2. Standard Windows tooling
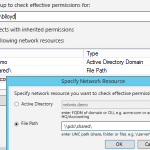
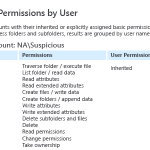
If we rely on the standard Windows tooling then right away we encounter the first problems. NTFS rights are granted to directories and files via one of the thirteen "special" rights, or several "simple" rights which amount to a combination of special rights. The users, groups, and permissions (Access Control Entries) together constitute the Access Control List for a file or directory. Because this information is directly linked to a directory or file but not centrally stored, a network administrator will state the need to check all the directory's one by one to come to an overview of rights. In addition, a user can inherit rights through membership in groups, which makes the whole thing even more complex and time consuming to get a realistic overview. Current versions of Windows offer a tab in the directory properties to determine the effective rights of a user, but unfortunately this option is only for an individual directory. There is also a number of command-line tools available that we will evaluate later.PowerShell
We have the option to use PowerShell, a scripting solution from Microsoft that enables special tasks to be performed by the operating system. One of these tasks is the Get-Acl cmdlet to get the security descriptor of a file or directory. In combination with the Get- ChildItem cmdlet to browse a folder structure, we can use a script to export all Access Control List Entries (ACE's) to a CSV file. The command powershell can be typed in the command line. PS appears before the command prompt and now the entire powershell script can be pasted and performed:Get-ChildItem "C:\MyFolder" -Recurse | Sort-Object FullName | %{
$Path = $_.FullName
$IsDirectory = $_.PsIsContainer
(Get-Acl $Path) | Select-Object `
@{n='Path';e={ "$Path, d=$IsDirectory" }},
@{n='Access';e={ [String]::Join("`n", $( $_.Access | %{
"$($_.IdentityReference), $($_.AccessControlType), $($_.IsInherited), $($_.InheritanceFlags), $($_.PropagationFlags), $($_.FileSystemRights)" })) }}
} | Format-list | Out-File -FilePath C:\temp\permission_export.txt -Encoding UTF8
A major advantage of PowerShell scripts is that the job is run on the remote server. Only the result is sent to the requesting machine through the network. We were disappointed with the performance of these tasks, scanning 500,000 local files took 32 minutes, 30% CPU, 1 GB memory and resulted in a CSV file of 150 MB. Other tools, such as Perdemia's Permission Analyzer, scans the same file information in 20 minutes as well as writing it to a database. PowerShell offers a lot of options and cmdlets to apply filters or additional tasks. For example, to skip inherited rights we can apply the line below in the preceding script:
@{n='Access';e={ [String]::Join("`n", $( $_.Access | ?{!$_.IsInherited} | %{
And to exclude files from the export we can use the following:
Get-ChildItem "C:\MyFolder" -Recurse | Sort-Object FullName | ?{ $_.PsIsContainer } | %{
But then? Then we have all rights in a CSV file, without considering the group membership. We can of course do some basic checks and there are also ways in a PowerShell to read the Active Directory for group memberships, but even then it remains difficult to get the right information and requires substantial manual development. If we look at the available tooling then we encounter a number of comprehensive management applications, as well as tools purely focused on reading access rights (ranging between $200 and $2500 USD depending on the license form) and a number of small free tools. The large packages are distinguished mainly in the extensive functionality, but do they also help us to provide the stipulated information requirements?
1. Introduction3. Largescale software packages
3. Largescale software packages
Netwrix Effective Permissions Reporting Tool en Auditor for Windows File Servers
Netwrix supplies the commercial tool Auditor for Windows File Servers and the free tool Netwrix Effective Permissions Reporting Tool. The free version gives the rights for a specific user or group. A big plus with this tool is that it incorporates the (nested) group memberships from the Active Directory in the list of rights. When you start the tool there is a possibility to specify a user or group and a list of directory paths, shared folders, or Active Directory objects. Then a scan can be started with which an HTML file is drawn up containing the rights found. The current Windows user is used to extract the Active Directory and the directories, it is therefore advisable to run the program as Domain Admin with enough read permissions on the file system. A strong point of the HTML view is that the origin of the rights is reported, through which group a user has obtained rights. On the other hand, the disadvantage of the tool is that no comprehensive filters can be applied (except hiding inherited rights) and that only a single user can be selected. Ideally, we would select a complete group of users of which we can see the (misplaced) rights. Also, the tool can not show all rights for certain directories, without having to select a user, and the only output is the HTML table. Despite these drawbacks, the tool can be useful as it is free to use and the link to the Active Directory can provide very helpful information.Besides the free tool Netwrix also offers Auditor for Windows File Servers tool starting at $8 USD per active user in the Active Directory. For a large organization this can quickly run up costs. The paid variant focuses on changes in the rights on the basis of the Windows Audit Log. Please note, all these tools rely on the native Windows Audit Log and require Auditing on Directory Objects to be switched on so when adjustments have been made an event record is created in the Windows audit log. This can have serious consequences for the performance and storage space within the network! Therefore, be selective when enabling this audit logging. For certain changes Auditor can send alerts for Windows File Servers, which might help in our sixth information requirement, consistently maintaining the security principles. As far as the revealing rights the paid tool is very limited. It can create an export of the rights per folder as they are stored on the file system, but it lacks the power of the free Effective Permissions Reporting Tool. A combination of these two tools with some more filtering capabilities would be an interesting solution. For now, we think the paid tool is a fairly expensive solution to extract the Windows Audit Log.
| Effective Permissions Tool | Effective Permissions Tool | Auditor for Windows File Servers | Auditor for Windows File Servers |
|---|---|---|---|
 |
 |
<
|

|
ManageEngine ADManager Plus
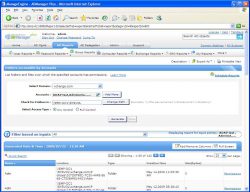
ManageEngine is a supplier of a number of management applications and ADManager Plus is one of the available modules focused on, among other things, NTFS rights. The price of this application depends on the number of helpdesk personnel and ranges between USD $795 and USD $14,995 per year. In a web interface, a number of Active Directory (AD) management tasks available and AD Reports containing a section NTFS Reports. Here we find the options "Permissions for Folders", "Folders accessible by Accounts" and "Non-Inheritable Folders". If we look at the rights per account, then we can select one or more accounts plus a network share. It occurs to us that it is unfortunately not possible to specify a local path or an admin share such as C$. In generating an overview the network share is scanned for rights for the selected user(s) including the groups to which this user(s) is a member of. This has the disadvantage that the entire file system is scanned for each query. So if we select other users the network share is scanned again, with all the network load and wait time that comes with that. The search results are presented as a list of folders in which we can show up to 100 at a time. The rights found are not instantly visible, but can be requested by clicking on the "Permissions" link (see screenshot). It is not immediately clear what rights have been found except by clicking on every folder in the Permissions link and looking at the popup view. An export to CSV, HTML, or PDF offers no additional details, because only the folders are exported without account information or rights. We find this insufficient for providing insight into the rights. We would like to immediately see the rights in an overview. ADManager Plus distinguishes itself mainly in the number of built-in reports for enumerating objects (such as users, groups, servers, and workstations) with certain characteristics. For providing insight into getting NTFS rights however, the application remains superficial and we lack basic functions in the review, such as extended filters, details in the search results, traceability (which permission in the displayed results belongs to which user from the filter) and detailed information in the exports. ManageEngine also delivers the application File Audit Plus, but this tool goes into file storage analysis and access audit reports (who has read and amended data and in which location) and doesn't help us with providing insight into getting the current NTFS rights.| NTFS reports | Folders accessible by account | Permission details |
|---|---|---|
 |
 |
 |
AdSysNet Active Directory Reporter
Active Directory Reporter by AdSysNet is available for $149 USD per year per domain and contains a section with NTFS Reports. After setting the correct domain controller, base OU and credentials we have the possibility to select numerous reports. In the section NTFS we find the reports "Folders usable by account" and "Permissions for given account". The first report requires an account name, a computer name and the choice of "Any control" or "Full control". We get to see a list of folders that our user has rights for. By clicking on the Permissions link a popup with the ACL of the folder appears. It is not entirely clear where the user's rights come from. We also see no further details in the main overview, except the path of the folders. For the second type of report we select a user and folder. In the search results we now see the group where the rights come from. We also see the rights that apply immediately, which is very useful. Regardless of the account name we can not set filters. In addition, we would also like to select a whole group of users, in order to check fully the rights and spot the exceptions. We also can't put a limit on the number of subdirectories and with every search the whole directory is checked which, with a major network share, costs quite a bit of time and bandwidth.| Permissions for a given account | Folders usable by account |
|---|---|
 |
 |
Varonis DatAdvantage
Another substantial tool is DatAdvantage by Varonis. Varonis is quite secretive about the price, probably for a reason, we read prices of $17,000 USD for a company with 100 people, or $26,000 for 250 Active Directory users to examples of $60 per active user with a top price of USD $400,000. This application is by far the most expensive on the list. Equally mysterious is the user manual, which we have not been able to find anywhere. DatAdvantage explores the questions "who gets what" and "who has made changes to what" and begins with scanning all ACL's on the file system. This information is stored in a Microsoft SQL Server database and in the course of the time is supplemented by Audit events. They use no native auditing of Windows, but have their own agent running on the file servers that transmits the changes to the database. Based on this combined information (ACL's and audit events) the application tries to make recommendations. It could be that certain users do not perform read actions on certain folders, an administrator can then consider access to these directories for this user. The tool also offers similar functionality with applications, but it is more involved in Data Access Governance.| Varonis DatAdvantage |
|---|
 |
PowerAdmin FileSight en ISDecisions FileAudit
We reviewed FileSight by PowerAdmin, but this application is aimed solely on changes that are made in the rights with associated alerts. The tool costs $599 USD per file server and would help us in the 6th information requirement, keeping consistency in the security principles, but because of the lack of reporting on the current rights we have left this tool out of the scope. The same goes for FileAudit by ISDecisions, priced at $826 USD per file server.Conclusion The abovementioned tools are part of larger packages and on the whole provide a range of different reports. Obvious reports serving as an overview of all kinds of different objects within the network with certain properties and some useful reports based on the native Windows Auditing. NTFS rights are part of this, but the real analysis on the relationship between users, group memberships, and NTFS rights remains very superficial in these tools. We miss the possibility to filter on multiple users to segment users and a piece of traceability to see where exactly the rights come from. Tracking changes in rights is good for compliancy, but by monitoring everything the question remains if the NTFS rights are still compliant with the design for data protection! Let’s look at some smaller tools specifically targeted at reporting NTFS rights.
2. Standard Windows tooling4. Focused commercial tooling
4. Focused commercial tooling
NETsec Permission Reporter
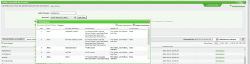
German company NETsec offers the tool Permission Reporter 4.0. We have no price information for this tool, but the price is set on the basis of the number of Active Directory users. In the application, a number of profiles can be created, consisting of a directory path with a subdirectory depth and the setting to determine which files are included in the scan or not. Each profile can then be scheduled or run immediately, which means that all rights from the directory are stored in the database. This can be a local database or a remote MSSQL server. Scanning 50,000 local directories/files to a local database took us 17 minutes (around 3,000 files per minute, with the speed in the second half of the scan dropping significantly). The design of the planning of profiles and saving data in a database appeals to us, only the scan speed dropped off so fast that we ask ourselves how the application handles larger amounts of data. In comparison, other tools with an underlying database scan the same directory within 2 minutes. The scan picks up 100% CPU (Intel i7-3520M CPU), it is therefore advisable to not refresh the profiles on the file server or at least to perform this outside office hours. Following the scan we can view the profile in a "File System Point of View" or an "Active Directory Point of View". In the first view, we are very pleased that the ACL information is not instantly included in the folder tree, but is shown in a section under the tree. A useful addition is that the groups in the ACL can be unfolded to display the members. In the second view an AD user can be selected, after which directories with rights are shown in the lower part. Nested group memberships of the user are included, only unfortunately we can not see the origin of the rights in the overview. Also the folders without rights are shown, which makes an unnecessarily large overview with a lot of irrelevant data. In the toolbar we see an option to edit the rights, but this simply opens the file properties in Windows Explorer.With all the directory information in the database, we would like to apply filters so that we can take advantage of the power of a database without overusing the network. Unfortunately, the application has no filtering capacity other than to filter the account name of a user.
| AD point of view | File point of view |
|---|---|
 |
 |
PermissionMe NTFS Plus
Another tool we come across is NTFS Plus by PermissionMe, priced at $149 USD per year. Also this application starts with defining profiles, which can be refreshed manually. There is no documentation about the application, other than the webpage, it is therefore not entirely clear where and how the data is stored. In any case, we see no possibility of linking a database or to schedule a scan automatically. However, it is good to that search results can be displayed in different ways: Standard ACL, Breakout Groups, Users Only and Effective Rights. Filters can be applied to, among other things, account, group, department, and simple rights. We see no possibility to filter based on multiple rights, other than a single simple permission. The department filter is a very useful filter we do not come across much in other tools. The tool also offers some features to customize rights and group memberships. It strikes us that the scan can not be limited to the number of levels of subdirectories and the data can only be stored locally.| View permissions | Edit permissions |
|---|---|
 |
 |
KeyMetricSoftware Permissions Reporter
KeyMetricSoftware's Permissions Reporter scans the folders and stores the results in the memory. This application has no underlying database, the results can only be stored in an XML file, to be loaded later. When the scan is complete, we can browse through the folders in a tree structure or as a flat table. In the tree view the ACL information (users with their rights) is interwoven between the folders. We feel this is what leaves clutter. Especially since even users who do not match the filters are highlighted in the overview with a light gray color. The so-called "post-scan filters" can be applied to the dataset in a user-friendly way and offer options to filter using account name, rights, special rights and inheritance. It occurred to us that the user's memberships are not taken into account and the rights of these groups also don't appear in the overview. As an alternative we could use the filter "account name in nested group", but if we run and HTML rapport we see all members of the matching groups instead of our selected user. This results in an HTML report with two million lines for some folders (think of groups such as Domain Users etc.). We are still not completely sure of how this might work. The tool does provide a useful compare function to compare two XML files (exports a scan) with each other, so the changes within a period can be viewed. The price is between $69 and $2,200 USD depending on the license use (single user, company-wide or country-wide).| Folder tree | Folder report | Filters |
|---|---|---|
|
 |
 |
Cjwdev NTFS Permissions Reporter
Cjwdev has the tool known as NTFS Permissions Reporter, a striking resemblance with KeyMetricSoftware's Permissions Reporter. Both tools have the same appearance and functional design. Cjwdev's tool, like KeyMetricSoftware, loads the folder information from memory instead of from a database, which means that first the entire network needs to be scanned on startup of the application. There is also the possibility to store the results to a file, so that this information can be loaded faster on startup of the application. In addition, command-line parameter can be used automatically to create an export to HTML, for example. Files are not included in the scan or the review, only the folders. After scanning the directory the folder tree is shown with the ACL information. The same ACL of the selected folder is in a panel on the right, we wonder why the ACL information is displayed in the folder tree and what the added value is of the panel on the right. Now 80% of the screen remains unused. Adding filters is done in the same way as in KeyMetricSoftware, only Cjwdev, fortunately, offers the possibility to include nested group memberships in an account filter! We also see a column in the HTML report "From group", with which we maintain the relationship between our users in the filter and the nested group memberships. Unfortunately we do not see this information reflected in the tool itself. So if we filter on multiple users and get to see the folder tree with nested groups, which rights and groups belong to which user from our filter? It is a piece of traceability in the search results we are missing here. The cost of the application ranges between $149 and $620 USD, depending on the scope of the license.| Folder tree | Apply filters | Filter on account name | All filters |
|---|---|---|---|
 |
 |
 |
 |
Largescale software packages5. Freeware
5. Freeware
SysInternals AccessEnum
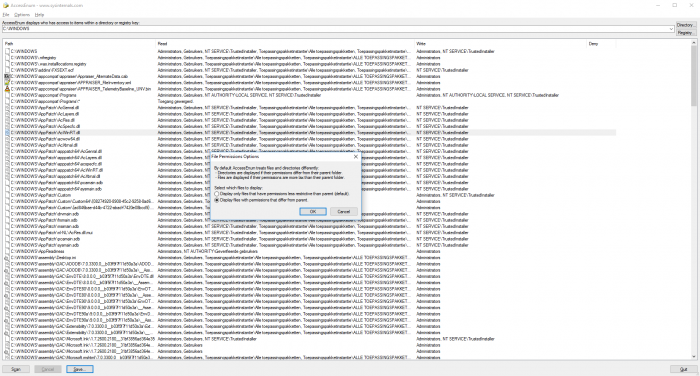
AccessEnum is a free tool by SysInternals, now part of Microsoft. In the tool a directory path can be specified, then a scan can be started. The results are shown in a table with three columns, Path, Read, Write and Deny. Directories are displayed if their permissions differ from their parent folder and files are displayed if their permissions are more lax than their parent folder. It offers two options for the files, display files that have permissions less restrictive than parent (default) and display files with permissions that differ from parent. The results can be exported to a CSV file and the results can be compared to a previously saved CSV file. In this way the modified rights over time can be easily traced. Furthermore, the tool does not provide any filter options and distinguishes only the read and write permissions. Further details of rights (delete, modify, full control and special permissions) are missing. Also there is no link to the Active Directory and group memberships are not so read out. The tool is especially suitable for 'low-level' exporting of the rights, to subsequently make basic filters in a program such as Excel.| AccessEnum |
|---|
 |
SysInternals AccessChk
In order to get more details on specific rights on the system a free command-line tool AccessChk by Sysinternals can be used. The tool has no graphics interface, but can therefore easily be run periodically with Windows Scheduled Tasks. The tool has some filters for account name and ignoring inherited permissions, but again only those rights that are directly linked to the account are shown. Without the group memberships of the user. By default, the tool only has the rights Read, Write or Read + Write, but with the parameter-l the full Access Control Entry can be shown. This is a low-level view of the rights, but does include all rights information with inheritance flags and whether an ACE was granted directly or retrieved through a parent folder.| Account filter | ACL info |
|---|---|
|
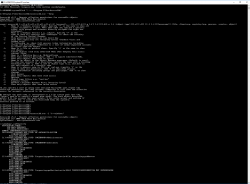 |
Solarwind Permissions Analyzer for Active Directory
Solarwind Permissions Analyzer for Active Directory displays the effective rights for a specific user or group. A strong point is that a domain controller can be configured to retrieve group information about the user. Nested groups are included in the overview. Unfortunately, we found out that only the rights to a specific network share appear, without the subdirectories. It is also not possible to specify a local path. We do see a distinction between rights granted and rights acquired directly through group membership, which of course is beneficial when it comes to the traceability of rights. Furthermore, the tool remains an alternative for the Windows Effective Permissions tab we still need to inspect each directory individually, which makes it not entirely useable in terms of gaining insight into all effective rights of a user of a group.| Solarwind Permissions Analyzer for Active Directory |
|---|
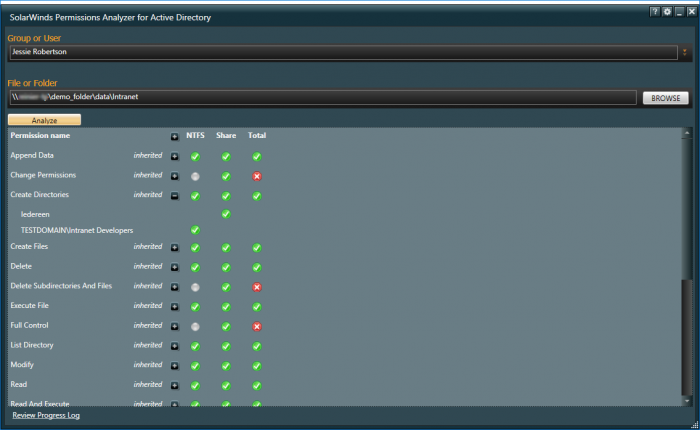 |
SomarSoft DumpSec
SomarSoft's DumpSec is another free tool to display rights in a simple table. This tool also has the capacity to display only the folders and files that differ from the parent folder. The results can be exported to CSV, but unlike AccessEnum the results can not be compared to a previous scan. DumpSec also offers the possibility to filter for a text, account name or simple permission. In addition to an overview of the tool it also provides a summary of user rights, groups, policies, and services. There is no link with the Active Directory and group memberships of the user are not included in the list of rights. DumpSec does have some command line parameters, so that exports can be made with Windows Scheduled Tasks periodically.| DumpSec |
|---|
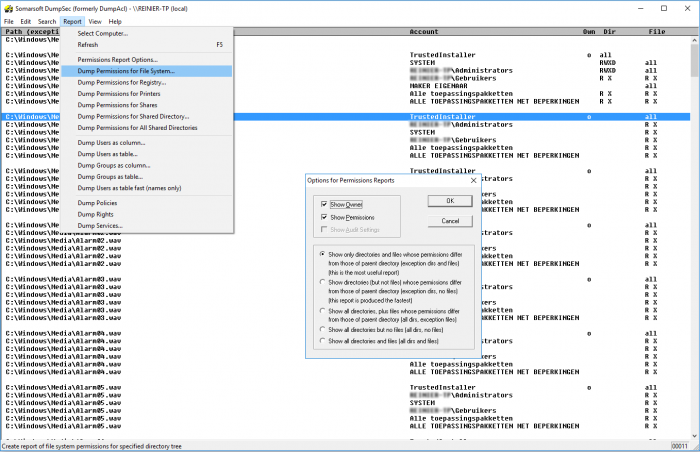 |
Cacls, Xcacls, Icacls en SetACL
Cacls and Xcacls are native command-line tools from Microsoft Windows for replacing and editing the Access Control List. Both tools have been replaced by Icacls (Integrity Control Access Control List) that is available from Windows Server 2003 SP2 or Windows Vista or later. Please note, all known versions of Icacls have a serious bug on objects with protected ACLs, Icacls ignores this protection, resets/destroys the protection and applies/propagates the inheritable permissions from the parent to the object and its children. A number of examples of Icacls are:icacls name /save aclfile [/T] [/C]
Stores the acls for all matching names into aclfile for later use with /restore. /T indicates that this operation is performed on all matching files/directories below the directories specified in the name. /C indicates that this operation will continue on all file errors.
icacls Test1 /grant User1:(d,wdac)
To grant the user User1 Delete and Write DAC permissions to a file named "Test1".
SetACL by Helge Klein is another command-line tool, which, like COM DLL component can be used in an individual application. It supports paths longer than 260 characters, something a lot of tools fail to do. The tool can be very useful for adjusting large amounts of rights or making backups. Removing all rights for a specific user might be done in this way:
SetACL.exe -on "c:\\" -ot file -actn trustee -trst "n1:UserOrGroup;ta:remtrst;w:dacl,sacl" -rec cont_obj -ignoreerr
Removes "UserOrGroup" from the ACLs of all files on drive C:.
Or the migration of rights:
SetACL.exe -on "\\server1\share1\users" -ot file -actn trustee -rec cont_obj -trst "n1:domain1\user1;n2:domain2\user2;ta:cpytrst;w:dacl"
This command copies all ACEs belonging to "domain1\user1" to "domain2\user2" resulting in a duplication of permissions: after the process domain2\user2 has the same permissions as domain1\user1. This might be useful in a migration scenario where users from domain1 are migrated (copied) to domain2.
See more examples here. SetACL also boasts an impressive user interface in the form of an application named SetACL Studio. The application is a nice replacement for the Windows ACL Editor in Windows Explorer, but it doesn't really help us in getting a rights overview by user or group. The same applies to the previous command line tools, they are useful tools to perform bulk actions but for providing insight into the current rights it needs to be filtered manually by text file with all the ACL information.
| SetACL Studio |
|---|
 |
Focused commercial toolingConclusion
6. Conclusion
Let's take a look to see if we have managed to answer any of our information requirement related questions. We can see that large software packages focus mainly on auditing of the environment, who changed what and when. Gaining insight into getting the current NTFS rights remains quite superficial. We miss advanced filters, the involvement of multiple users in an overview and the traceability of rights. Maintaining consistency in the security design is addressed in these tools in the form of alerts when changes are made. The point is that every alert must be reviewed manually by a system administrator to see what the impact is of the change. If this is at all possible, since a system administrator can also not always predict the side-effects of a change. We want the ability to, at any moment, validate that the following example principles actually apply within the network:- Only members of the Group HR allowed to read in the directory \\server01\data\employees
- External employees have no read rights in \\server01\data\customers
- Only members of Project Management may remove data from \\server01\data\projects
The smaller commercial tools offer a lot of possibilities to get an overview per user and to export to a report. A single tool shows where the rights come from (through which group memberships), but most tools only show the effective rights whereby you, as a system administrator, still don't have an overview. Only the NETsec Permission Reporter tool offers the possibility of a database. The scanning speed was so fast, that we wonder whether scanning a million files is going to work at all. The other targeted commercial tools scan the network upon boot up and load all the information in the memory, which of course results in the necessary network traffic, wait time and memory usage. Cjwdev NTFS Permissions Reporter offers the most comprehensive and most user-friendly way to apply filters. The presentation of data, like many other tools, appeals less to us. The rights in the directory tree are not available at a glance, and all the Access Control Entries are between the folders. We're also missing an overview of effective and indirect rights and the origin of these rights per user.
The free tools are particularly suited to make a bulk export of the current rights. Indirect rights (through group memberships) are not included, so it is quite difficult to get a complete overview of effective rights for a user. The rights will have to be combined with group membership manually from the Active Directory and all filtering capabilities and reports themselves will have to be built.
Perdemia's Permission Analyzer is a targeted tool to gain control on the proliferation of NTFS rights. It offers a unique way to apply filters, look at results from different angles and can automatically check on the consistency of security principles by setting its own rules. Here we'll discuss some examples to see how the application works.
5. Freeware7. Approach with Perdemia's Permission Analyzer
7. Approach with Perdemia's Permission Analyzer
More than ten years ago, Perdemia's Permission Analyzer started as an application to reveal the NTFS rights per user or group. Now, the application has been completely rebuilt to version 2, in order to better fulfill information requirements stated in the Introduction. Permission Analyzer was rebuilt with the focus on performance and large amounts of data. The directory information and user information is therefore not all loaded into memory and it does not scan the network for every search, but it uses a database to gather all the information together and to apply filters. It's standard to use an embedded database (H2), but out-of-box the application also supports MSSQL Server, Oracle, MySQL, DB2, PostgreSQL and Derby.Scanning the network
The application provides two 'views' from the menu, the Scan View and the Report View. In the Scan View the scan is configured by selecting the desired directories and OU's from the Active Directory. The directories can be added as network share, local directory, simply a server name (a search for network shares will automatically happen), or a text/zip file generated by a Powershell script included or EMC Isilon export from a NetApp filer. Incidentally, a Scan Agents can also be used that run locally on a file server and store the scan results in a central database. The Active Directory OU's are used to scan for group memberships. A scan can also be started automatically with various command-line parameters, which periodically refreshes the data.
Creating reports
After the scan is complete the database can be used to make overviews. The Report View of the application displays the initial folder tree containing a summation of the rights found per directory or file. The folder icon indicates what rights are found and the columns next to a directory show the special rights. Without applying filters, the permission will mainly be set to "Full Control" with all the special rights, but after applying filters on a user or group, the unwanted rights can be viewed at a glance. In order to not clutter the folder tree the users are not instantly displayed in the folder tree, but rather across in four tabs under the folder tree:- Effective permissions: displays the effective rights of all users and groups in the selected folder that match the filter criteria. Each user or group can be folded out to see where the rights originate from.
- ACL on the file system: shows the rights (Access Control Entries) as they appear on the file system. This corresponds with the Security tab in Windows Explorer and includes the possibility to adjust rights from within the application.
- Trace the origin of permissions: provides the ability to create a user or group to pin down through which group memberships and parent folders the rights have been obtained.
- All matching users and groups: the previous tabs display information for the selected directory. This tab displays all unique users and groups that are found in the overview. Each user or group can be folded out to see where the rights are found and through which group.
 Through these four angles we can easily get answers to the first five information requirements. We can instantly view effective rights on all directories, we see per directory and user where the rights come from and we can filter out all the users of a particular group without losing the relationship between the rights and users. The latter helps us with the 5th information requirement ("What are the right for all users of a specific group and where are the exceptions?"). Finally, we want to know which users or groups are involved in the unwanted rights within the search results. By including multiple users/groups as a filter, or a filter of the "All members from group" type, in one bulk check an overview is created for a large group of users including nested group memberships. With the Effective Permissions and All matching users and groups tabs, we can subsequently zoom in on individual users.
Through these four angles we can easily get answers to the first five information requirements. We can instantly view effective rights on all directories, we see per directory and user where the rights come from and we can filter out all the users of a particular group without losing the relationship between the rights and users. The latter helps us with the 5th information requirement ("What are the right for all users of a specific group and where are the exceptions?"). Finally, we want to know which users or groups are involved in the unwanted rights within the search results. By including multiple users/groups as a filter, or a filter of the "All members from group" type, in one bulk check an overview is created for a large group of users including nested group memberships. With the Effective Permissions and All matching users and groups tabs, we can subsequently zoom in on individual users.
The last information requirements is to run checks to keep the access rights consistent. Instead of notifying system administrators for each change, Permission Analyzer offers another solution. A set of filters can be stored as Policy in order to periodically check for unwanted rights. If search results are found on a Policy, the system administrator can be notified by email, with an HTML report of the rights found as an attachment. Also, the list of Policies with their status is available within the application. Loading of a Policy gives the possibility to zoom in on the results and thus solve the cause. Example: We make a policy in which it is stated: "Nobody from the group Freelancers can edit project data" We want to create a report in which we get to see the unwanted rights so that we can save the filters as Policy. We add a member filter of the type "All members from group" and we select the group Freelancers. Then we add additional filters to the rights (we want to allow read access), and we report on the scopes folder \\dataserver01\projects:
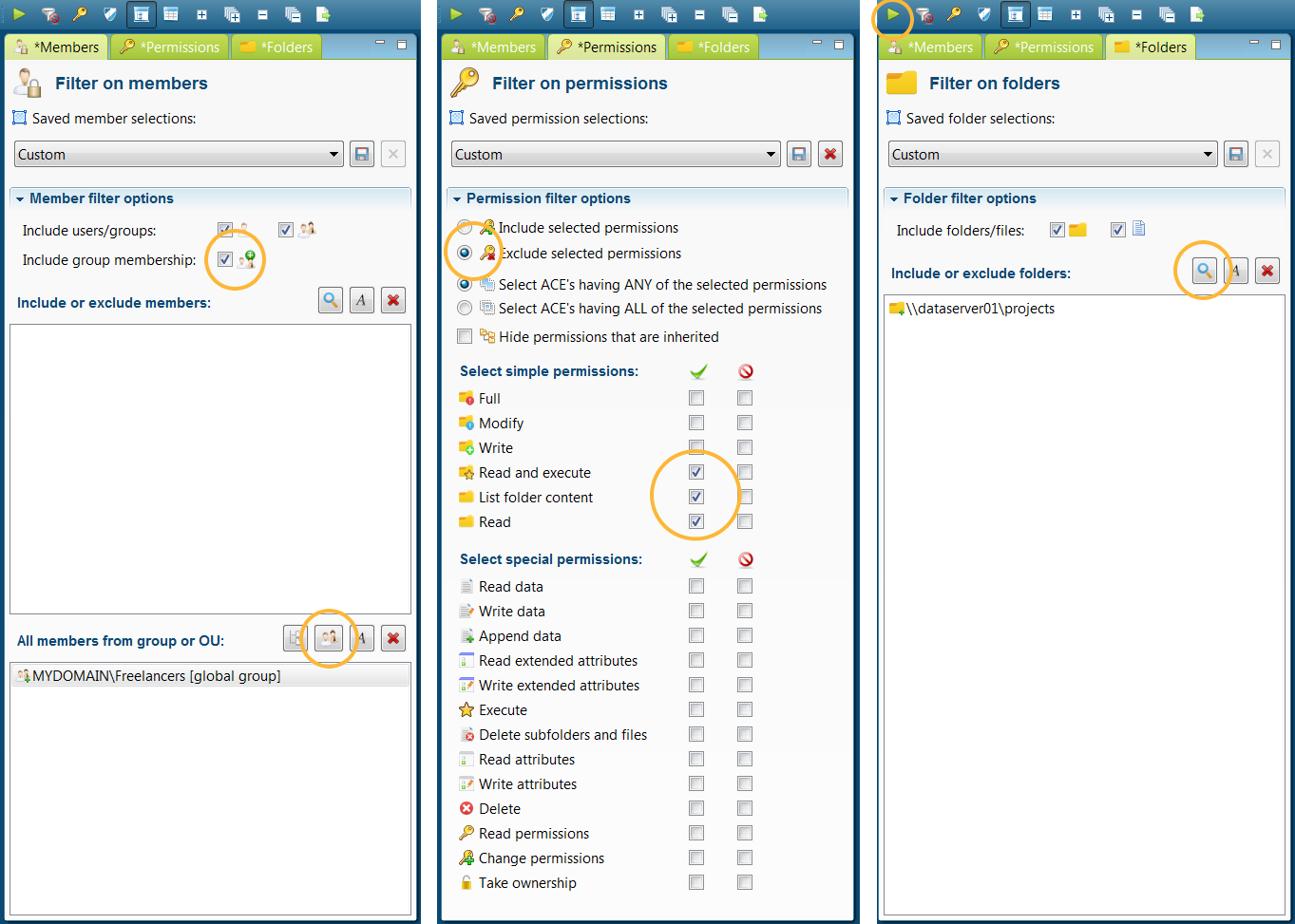
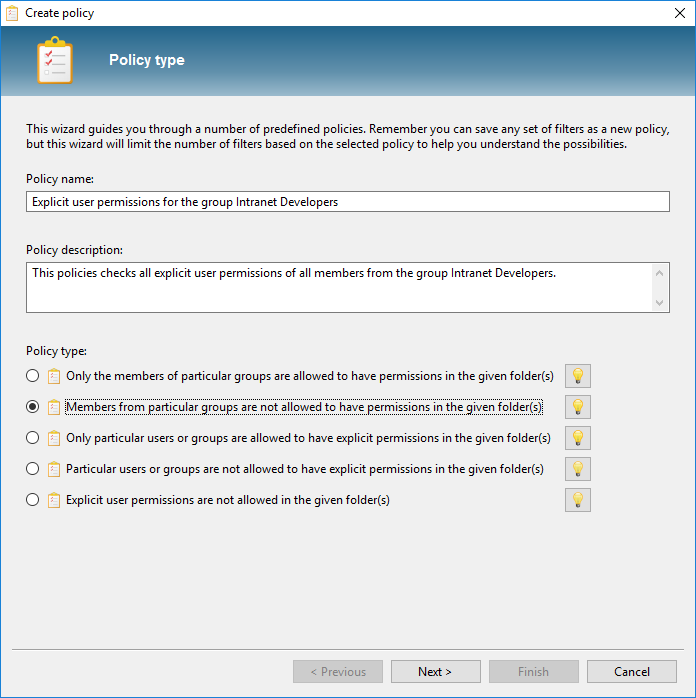
Tip: Use the Policy Wizard to get acquainted with the various filter options:
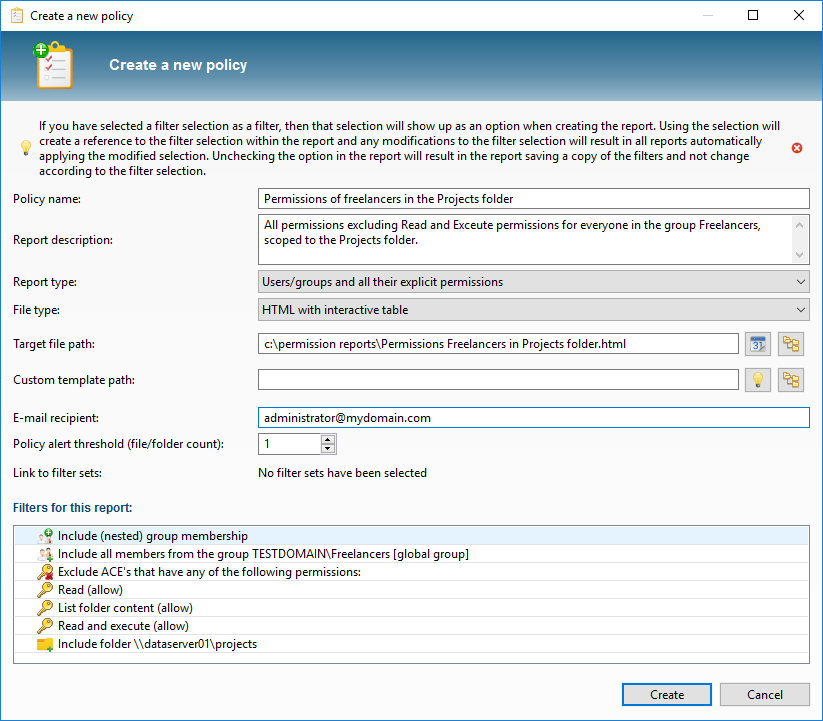
The listing now shouldn't display any search results, which means that no unwanted rights have been found. We now store the filters as Policy:
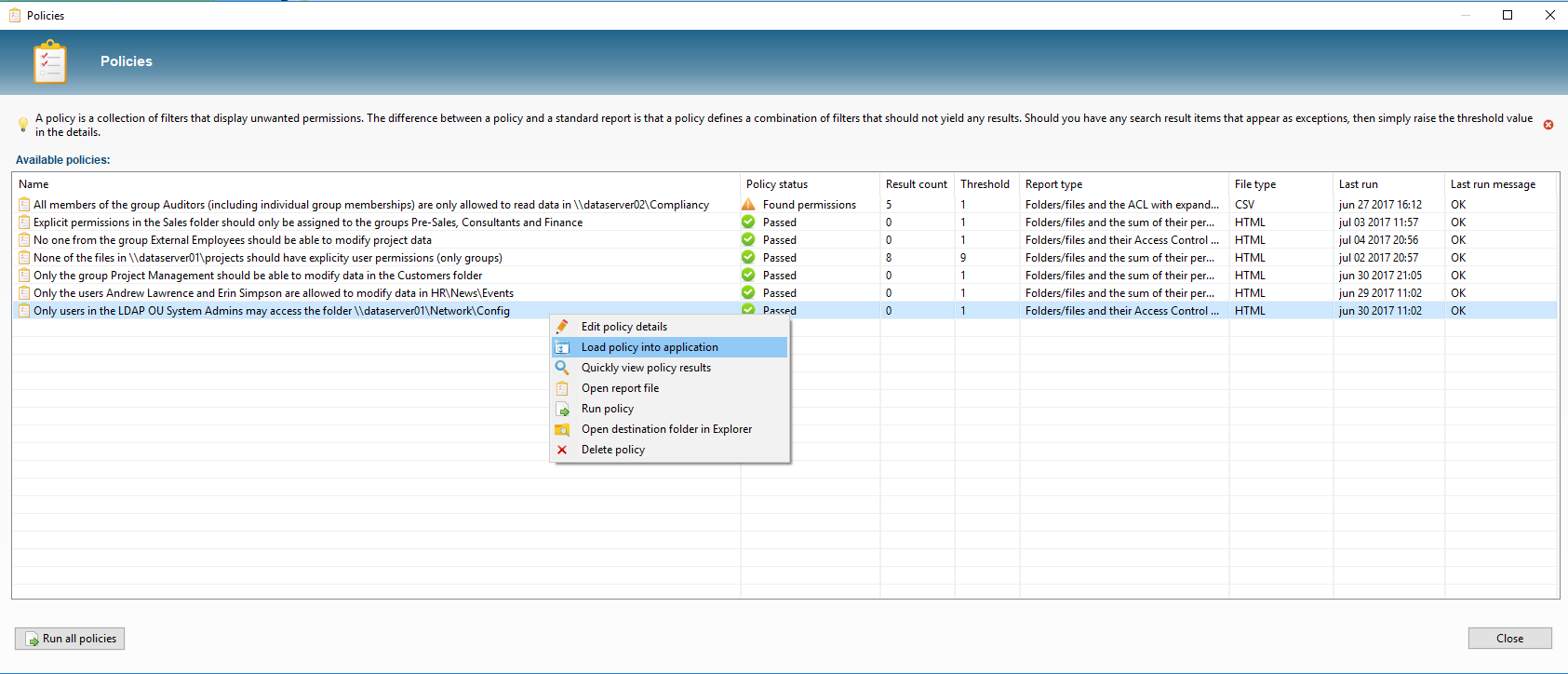
By regularly running the policies via the parameters -scan and -allPolicies, we can periodically check the rights for consistency, without having to check each change in the folder structure manually. In the overview of Policies we can see the status of our rules at a glance and we can zoom in on the unwanted rights by loading a policy in the application:
Audit Dashboard
In addition to regularly running policies we can immediately discover a number of improvements for the Data Access Governance via the Audit Permission Analyzer's dashboard. This dashboard shows 18 different charts including a top 25 of users who have the most explicit rights (rights that may have to be regulated through a group membership), a top 25 of users with the most group memberships, the ratio between direct and indirect group membership, directories with the most explicit rights and much more. Many of these statistics instantly detect where the possible risks are if someone manages to get unauthorized access to the system.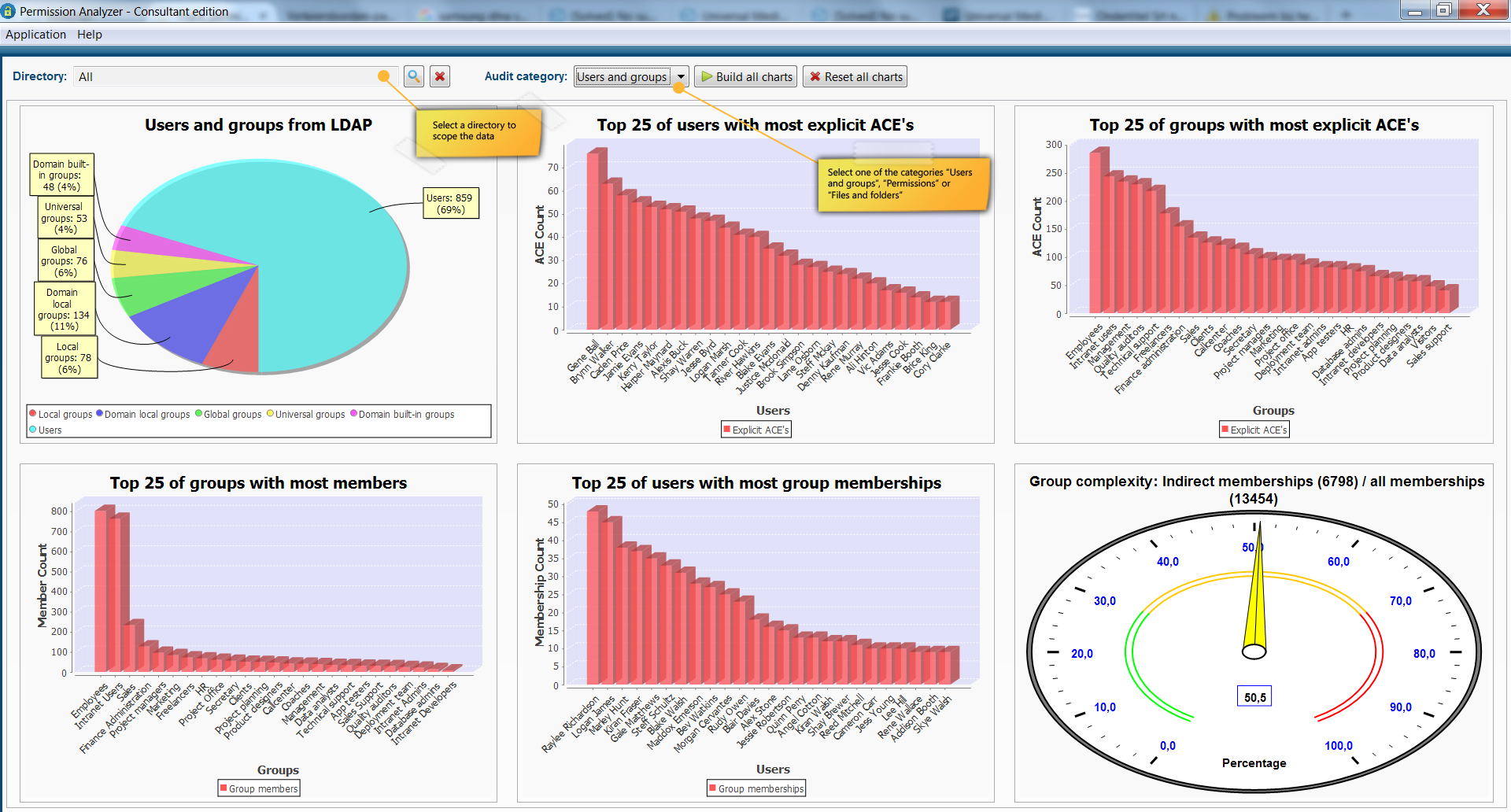
The price of Permission Analyzer depends on the number of users and groups that is scanned and varies between $149 and $499 per year. A license is valid for a single machine on which the application is installed (not the number of servers scanned). A trial version is available online, as well as time-limited versions of each of the Permission Analyzer editions.
6. Conclusion
